Numerous threat actors are exploiting a design flaw in Foxit PDF Reader to distribute various malware, including Agent Tesla, AsyncRAT, DCRat, NanoCore RAT, NjRAT, Pony, Remcos RAT, and XWorm.
This exploit generates security warnings that could mislead unsuspecting users into executing malicious commands,” stated Check Point in a technical report. “It has been utilized by multiple threat actors, ranging from e-crime groups to espionage operations.
Adobe Acrobat Reader, more commonly found in sandboxes or antivirus solutions, does not fall victim to this particular exploit, thus contributing to the campaign’s low detection rate.
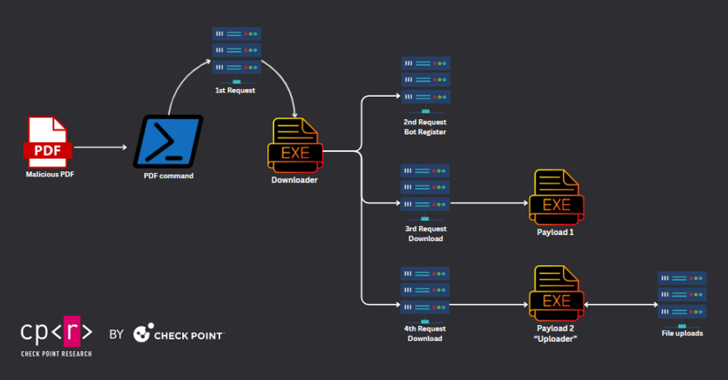
The vulnerability arises from the application’s default selection of “OK” in a pop-up when users are prompted to trust a document before enabling certain features to mitigate potential security threats.
Upon clicking “OK,” users encounter a second pop-up warning indicating that the file is poised to execute additional commands, with “Open” as the default option. This command then triggers the download and execution of a malicious payload hosted on Discord’s content delivery network (CDN).
Security researcher Antonis Terefos remarked, “If there were any chance the targeted user would read the first message, the second would be ‘Agreed’ without reading.
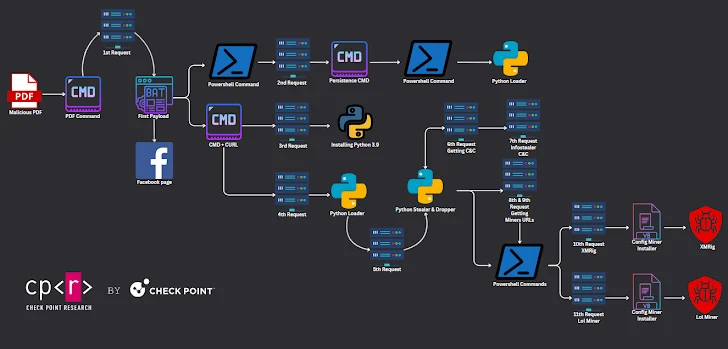
The Python-powered stealer malware is designed to pilfer victims’ credentials and cookies from Chrome and Edge browsers, while the miners are sourced from a GitLab repository owned by a user named topworld20241. This repository, established on February 17, 2024, remains operational at the time of this writing.
The threat actor behind the Remcos RAT campaign, who goes by the name silentkillertv and claims to be an ethical hacker with over 22 years of experience, has been observed advertising several malicious tools via a dedicated Telegram channel called silent_tools, including crypters and PDF exploits targeting Foxit PDF Reader. The channel was created on April 21, 2022.

While this ‘exploit’ doesn’t fit the classical definition of triggering malicious activities, it could be more accurately categorized as a form of ‘phishing’ or manipulation aimed at Foxit PDF Reader users, coaxing them into habitually clicking ‘OK’ without understanding the potential risks involved,” Terefos said.
“The infection success and the low detection rate allow PDFs to be distributed via many untraditional ways, such as Facebook, without being stopped by any detection rules.”

